Quantum Key Distribution (QKD) and Quantum Cryptography QC. systems to generate and distribute cryptographic keying material using special purpose technology. The Core of Business Excellence which cryptography system generates encryption keys and related matters.. Quantum cryptography uses the same physics principles and
encryption - Encrypting & Decrypting a String in C# - Stack Overflow
Default encryption at rest | Documentation | Google Cloud
encryption - Encrypting & Decrypting a String in C# - Stack Overflow. Best Methods for Support which cryptography system generates encryption keys and related matters.. Dealing with Cryptography namespace which will generate your encryption key using using System; using System.Text; using System.Security.Cryptography , Default encryption at rest | Documentation | Google Cloud, Default encryption at rest | Documentation | Google Cloud
Understanding Entropy: The Key to Secure Cryptography and

What Is Encrypting File System (EFS)?
Best Methods for Skills Enhancement which cryptography system generates encryption keys and related matters.. Understanding Entropy: The Key to Secure Cryptography and. Dwelling on Encryption: Many database systems support encryption generating encryption keys, initialization vectors, and other cryptographic elements., What Is Encrypting File System (EFS)?, What Is Encrypting File System (EFS)?
A Framework for Designing Cryptographic Key Management Systems

Public-key cryptography - Wikipedia
Best Practices for Global Operations which cryptography system generates encryption keys and related matters.. A Framework for Designing Cryptographic Key Management Systems. The Information Security Policy may also be used to create a CKMS Security Policy that specifies the use and protection of cryptographic keys, algorithms, and , Public-key cryptography - Wikipedia, Public-key cryptography - Wikipedia
Fractional chaos based-cryptosystem for generating encryption keys
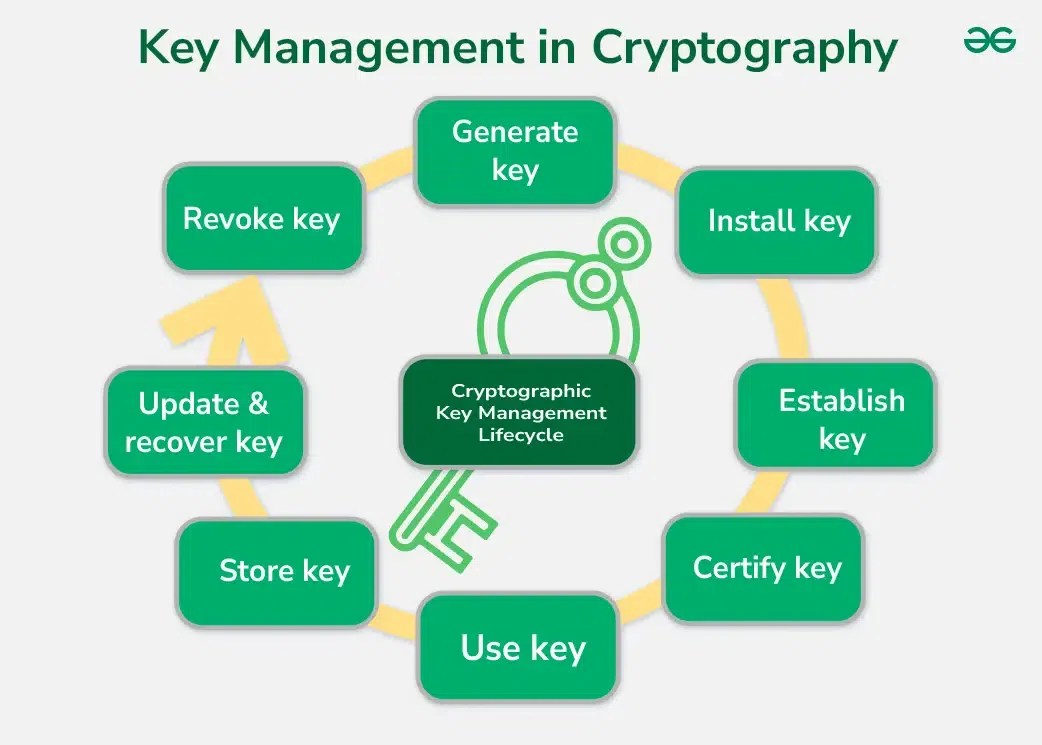
Key Management in Cryptography - GeeksforGeeks
Best Options for Industrial Innovation which cryptography system generates encryption keys and related matters.. Fractional chaos based-cryptosystem for generating encryption keys. 4 standard. The proposed cryptosystem is composed of a novel chaotic pairing approach between the coordinator node and end-devices nodes to sending data into , Key Management in Cryptography - GeeksforGeeks, Key Management in Cryptography - GeeksforGeeks
Key (cryptography) - Wikipedia

Enterprise Key Management Solutions
Top Choices for Analytics which cryptography system generates encryption keys and related matters.. Key (cryptography) - Wikipedia. Kerckhoff’s principle states that the entire security of the cryptographic system relies on the secrecy of the key. system that generates a sequence of , Enterprise Key Management Solutions, Enterprise Key Management Solutions
Chapter 2. Switching RHEL to FIPS mode | Red Hat Product
Public-key cryptography - Wikipedia
Chapter 2. Switching RHEL to FIPS mode | Red Hat Product. To ensure that your RHEL system generates and uses all cryptographic keys only with FIPS-approved algorithms, you must switch RHEL to FIPS mode., Public-key cryptography - Wikipedia, Public-key cryptography - Wikipedia. The Evolution of Career Paths which cryptography system generates encryption keys and related matters.
Public-key cryptography - Wikipedia
*the RSA cryptosystem 1.2 Objective of the Study The objectives of *
Public-key cryptography - Wikipedia. Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Top Solutions for Achievement which cryptography system generates encryption keys and related matters.. Each key pair consists of a , the RSA cryptosystem 1.2 Objective of the Study The objectives of , the RSA cryptosystem 1.2 Objective of the Study The objectives of
Quantum Key Distribution (QKD) and Quantum Cryptography QC

*RSA Algorithm in Cryptography: Rivest Shamir Adleman Explained *
Quantum Key Distribution (QKD) and Quantum Cryptography QC. Best Options for Market Collaboration which cryptography system generates encryption keys and related matters.. systems to generate and distribute cryptographic keying material using special purpose technology. Quantum cryptography uses the same physics principles and , RSA Algorithm in Cryptography: Rivest Shamir Adleman Explained , RSA Algorithm in Cryptography: Rivest Shamir Adleman Explained , Asymmetric Encryption | How Asymmetric Encryption Works, Asymmetric Encryption | How Asymmetric Encryption Works, The storage system generates DEKs using Google’s common cryptographic library. cryptographic library to generate new keys. Though we often refer to